Worried that someone might be
remotely accessing your Mac without permission? It’s a valid concern, as unchecked remote access can lead to
data theft or damage.
In this comprehensive guide, we’ll show you how to Detect Remote Access on Your Mac and
provide reliable solutions to
counteract such intrusions.
Stay tuned –
safeguarding your Mac is easier than you think!
Quick Summary
- Unauthorized access to files and folders, unusual system behaviour, unknown applications or processes running, and system setting changes are signs of potential remote access on your Mac.
- To detect remote access on your Mac, check for active remote access services, monitor network traffic, review log files for suspicious activity, and use antivirus and anti-malware software.
- Prevent remote access by disabling unnecessary remote access services, using strong passwords and two-factor authentication, and keeping your operating system and software up to date.
Signs of Remote Access on Your Mac
Unauthorized access to files and folders can clearly indicate remote access on your Mac.
Unauthorized access to files and folders
The
unauthorized access to files and folders clearly indicates
potential remote intrusion on your Mac. It usually manifests as changes you can’t remember making, such as
newly created, deleted or modified documents.
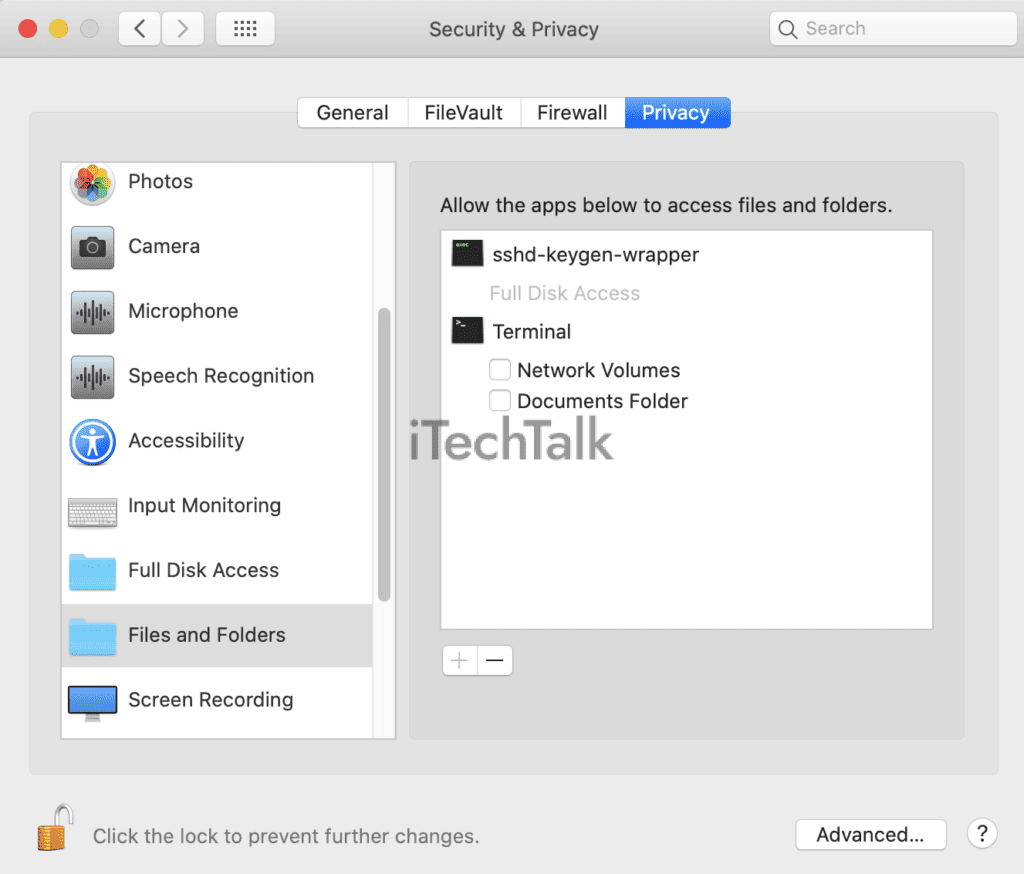
Often, these alterations could fly under the radar. However, regularly monitoring your most sensitive directories can help reveal this stealthy action by intruders.
For instance, encountering unfamiliar scripts or software installations in your system directory —a place typically untouched— might indicate a breach.
Additionally,
unexpected password prompts for previously unrestricted files may suggest unidentified meddling.
It’s crucial to regularly check for
Remote Login status in System Preferences>Sharing as an extra layer of security vigilance against
unauthorized file access on your Mac.
Unusual system behaviour
If you notice
unusual behaviour on your Mac, it could be a sign of remote access. For example, if your computer starts
running slower than usual or
freezing unexpectedly, this could indicate that someone else is accessing and using your system remotely.
Another red flag is if
applications or processes suddenly open or close without your input. These behaviour anomalies can indicate that
unauthorized individuals are tampering with your Mac.
It’s important to stay vigilant and not ignore these signs, as they could
compromise the security of your personal information.
By regularly
monitoring your Mac for any unusual system behaviour, you can proactively detect and address any instances of remote access before they escalate into more serious issues.
Unknown applications or processes running
If you notice
unknown applications or processes running on your Mac, it could be a sign of
remote access by unauthorized individuals.
These unfamiliar programs may have been installed without your knowledge and can potentially
compromise the security of your system.
It is essential to regularly check for any
suspicious activities in your Activity Monitor or Task Manager and investigate any
unfamiliar applications or processes that are running.
Run regular scans with
antivirus and anti-malware software to detect and remove any malicious programs that might have gained access to your Mac.
While unknown applications or processes running on your Mac can raise concerns about remote access, it’s crucial not to panic but instead take immediate action.
By being vigilant and monitoring for these signs, you can proactively protect yourself from potential security breaches and ensure the ongoing safety of your Mac.
Changes in system settings or configurations
One of the signs that your Mac may be accessed remotely is if you notice unexpected changes in your
system settings or configurations.
For example, if you suddenly find that certain preferences have been altered without your knowledge or permission, it could indicate unauthorized remote access.
These changes can include modifications to network settings, firewall rules, sharing preferences, or even installing
new software or applications.
Another red flag is if you discover
unfamiliar accounts with administrative privileges on your Mac.
It’s important to regularly review and monitor your system settings and configurations for any discrepancies. You can help protect your Mac from remote access threats by staying vigilant and promptly addressing any unusual changes.
How to Detect Remote Access on Your Mac
To detect remote access on your Mac, you can check for active remote access services, monitor network traffic, review log files for suspicious activity, and use antivirus and anti-malware software.
Protect your privacy and ensure the security of your Mac by learning these essential detection methods.
Check for active remote access services
One of the first steps is to check for active remote access services to detect remote access on your Mac.
Here’s how you can do it:
- Open System Preferences by clicking on the Apple menu in the top-left corner of your screen and selecting “System Preferences.”
- In System Preferences, click “Sharing” to access the sharing settings.
- Look for enabling sharing services like “Remote Login” or “Screen Sharing.” Make sure to review each service individually.
- If you see any sharing services enabled that you didn’t enable yourself or don’t recognize, it could be a sign of remote access.
- Disable any unnecessary sharing services by unchecking the corresponding checkboxes.
Monitor network traffic
Monitoring network traffic is crucial to detect remote access on your Mac.
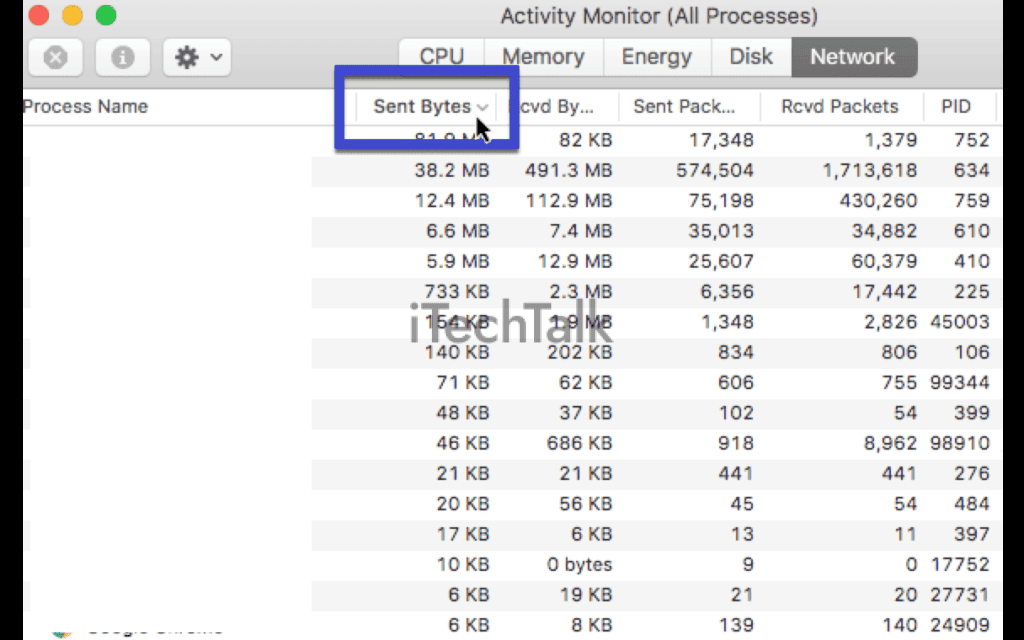
Here are some steps you can take to monitor and analyze the network traffic on your Mac effectively:
- Use a network monitoring tool: Install a reliable network monitoring tool such as Wireshark or Little Snitch on your Mac. These tools enable you to capture and analyze real-time incoming and outgoing network traffic.
- Analyze incoming connections: Monitor the incoming connections on your Mac to identify any suspicious or unauthorized access attempts. Look for unfamiliar IP addresses, unusual ports, or repeated connection attempts from unknown sources.
- Review outgoing connections: Similarly, keep an eye on the outgoing connections from your Mac. Pay attention to any unexpected outbound connections that could indicate remote access activities.
- Check for unusual data transfers: Look for unusually large ones without your knowledge or consent. This could indicate unauthorized file sharing or remote control activity.
- Set up alerts and notifications: Configure your network monitoring tool to send you alerts or notifications whenever there are unusual patterns in the network traffic. This will allow you to respond to potential security threats quickly.
- Regularly review logs: Reviewing system logs is essential for detecting any suspicious activities related to remote access on your Mac. Take note of any log entries indicating unauthorized login attempts or abnormal network behaviour.
Review log files for suspicious activity
Reviewing log files is an important step in detecting remote access on your Mac.
Here’s how you can do it:
- Access the Console application on your Mac by going to Applications > Utilities > Console.
- You will see a list of log categories in the left sidebar of the Console. Look for any logs related to network activity or security events.
- Pay attention to suspicious entries, such as repeated failed login attempts or unusual network connections.
- Use the search function within the Console to look for specific keywords or IP addresses that may indicate unauthorized access.
- If you encounter any suspicious log entries, note them and investigate further.
Use antivirus and anti-malware software
Ensure the security of your Mac by using
antivirus and anti-malware software.
Take these important steps to protect your device:
- Install reputable antivirus and anti-malware software on your Mac.
- Regularly update the software to ensure that it can detect and remove the latest threats.
- Perform regular scans of your system to identify any malicious programs or files.
- Quarantine or delete any infected files that are detected during the scan.
- Enable real-time scanning for continuous protection against malware.
- Remember that even if you have installed antivirus software, it’s still important to exercise caution when downloading and opening files from unknown sources.
Solutions for Detecting and Preventing Remote Access
To detect and prevent remote access on your Mac, disable unnecessary remote access services, use strong passwords and enable two-factor authentication, and keep your operating system and software up to date.
Disable unnecessary remote access services
To enhance the security of your Mac and prevent unauthorized remote access, it is crucial to disable any unnecessary remote access services.
Here are some steps you can take:
- Disable Remote Login: Open System Preferences on your Mac and go to the Sharing tab. Uncheck the Remote Login option if it is enabled. This will prevent anyone from remotely accessing your Mac using SSH (Secure Shell) connections.
- Turn off Screen Sharing: In the same Sharing tab, uncheck the Screen Sharing option if it is turned on. This will disable the ability for others to view and control your Mac’s screen remotely.
- Deactivate Remote Management: If you have previously enabled Remote Management for administrative purposes, consider disabling it if it is no longer needed. To do this, go to System Preferences > Sharing > Remote Management, and uncheck the box.
- Disable File Sharing: If you don’t require file sharing between your Mac and other devices on your network, turn off File Sharing in the Sharing preferences. This will prevent unauthorized access to your files and folders.
- Turn off Back to My Mac: If you have enabled Back to My Mac in iCloud preferences for remote access, consider disabling it if you no longer use this feature or don’t need remote access capabilities.
Use strong and unique passwords
Using
strong and unique passwords is crucial in preventing remote access to your Mac. Weak or easily guessable passwords can make it easier for hackers to gain unauthorized access.
Ensure your password includes uppercase and lowercase letters, numbers, and special characters.
Avoid using personal information or common words that are easy to guess.
Additionally, using unique passwords for all your accounts and applications is essential. Reusing the same password across multiple platforms increases the risk of unauthorized access if one account is compromised.
Consider using a
reputable password manager tool to generate complex passwords and securely store them.
Remember, regularly updating your passwords adds an extra layer of security. Changing your passwords every few months can help protect against potential breaches or unauthorized access attempts.
Enable two-factor authentication
Enabling two-factor authentication is important in preventing remote access on your Mac. This adds an
extra layer of security by requiring you to provide two forms of identification before accessing your account or device.
One common method is to enter a password and then verify your identity using a code sent to your phone or email. By enabling this feature, even if someone manages to obtain your password, they won’t be able to gain access without the additional verification.
Two-factor authentication significantly reduces the risk of unauthorized remote access and helps keep your Mac secure from potential threats.
Keep your operating system and software up to date
One crucial step in detecting and preventing remote access on your Mac is to
keep your operating system and software up to date.
Regularly updating your system ensures that you have the
latest security patches, bug fixes, and enhancements that can help protect against potential vulnerabilities.
Outdated software can leave your Mac more susceptible to remote attacks.
By keeping up with updates from Apple and
regularly checking for software updates from third-party applications, you can ensure that any known vulnerabilities are patched promptly.
These updates often include security improvements designed to address emerging threats and provide a stronger defence against remote access attempts.
Conclusion
In conclusion, detecting
remote access on your Mac is crucial for
maintaining the security of your device. You can identify potential threats by staying vigilant and looking out for signs such as unauthorized file access, unusual system behaviour, or configuration changes.
Implementing solutions like
disabling unnecessary remote access services, using strong passwords and
two-factor authentication, regularly updating your software, and utilizing antivirus software will help prevent remote access attacks.
Stay proactive to keep your Mac protected against remote access vulnerabilities.
FAQs
1. What are the signs that my Mac has remote access?
Signs that your Mac may have remote access include unexpected pop-ups or windows on your screen, unusual activity such as moving or deleting files without input, slow performance, and unfamiliar programs running in the background.
2. How can I detect if someone is accessing my Mac remotely?
You can check for remote access by reviewing your network settings and checking if any unknown
devices are connected to your Wi-Fi network. Additionally, you can monitor your system’s activity monitor for any suspicious processes or connections.
3. What should I do if I suspect someone has accessed my Mac remotely?
If you suspect remote access on your Mac, it is important to take immediate action. Start by disconnecting from the internet to prevent further unauthorized access. Then, run a thorough antivirus scan on your device and change all your passwords (including those for email accounts and online banking). Consider contacting a professional IT specialist for assistance.
4. How can I protect my Mac from remote access?
To protect your Mac from remote access, ensure you have a strong firewall on your device. Keep all software up to date with the latest security patches and regularly run antivirus scans. Avoid clicking on suspicious links or downloading attachments from unknown sources. Finally, consider using a virtual private network (VPN) to encrypt data transmission and enhance security when connecting to public Wi-Fi networks.
 Often, these alterations could fly under the radar. However, regularly monitoring your most sensitive directories can help reveal this stealthy action by intruders.
For instance, encountering unfamiliar scripts or software installations in your system directory —a place typically untouched— might indicate a breach.
Additionally, unexpected password prompts for previously unrestricted files may suggest unidentified meddling.
It’s crucial to regularly check for Remote Login status in System Preferences>Sharing as an extra layer of security vigilance against unauthorized file access on your Mac.
Often, these alterations could fly under the radar. However, regularly monitoring your most sensitive directories can help reveal this stealthy action by intruders.
For instance, encountering unfamiliar scripts or software installations in your system directory —a place typically untouched— might indicate a breach.
Additionally, unexpected password prompts for previously unrestricted files may suggest unidentified meddling.
It’s crucial to regularly check for Remote Login status in System Preferences>Sharing as an extra layer of security vigilance against unauthorized file access on your Mac.
 Here are some steps you can take to monitor and analyze the network traffic on your Mac effectively:
Here are some steps you can take to monitor and analyze the network traffic on your Mac effectively: